
Disaster Management Manual
A manual for practitioners and decision makers!

Disaster Management Manual
A manual for practitioners and decision makers!
Security threats are not that different from natural emergencies, except that they can cover a broader range of impacts, such as cyber/information technology (IT) attacks; chemical, biological, radiological, nuclear, and explosive (CBRNE) threats and terrorist actions, etc. Emergency and security responders must know the status of routes to and from the threatened area, both for responders and rescue assets. 1
The biggest challenge to the ITS system is a result of the increased value of ITS data and connectivity. Concerns about cybersecurity for ITS and traffic management deployments are related to both current technologies and as legacy systems, coupled with the growing trend to integrate ITS deployments with other networks. This combination has introduced new threats that have not been previously encountered in this domain.
The last few decades have witnessed the pervasive spread of computers, the Internet, and wireless technology. As these systems have become integral to our daily lives, so too has the potential for attacks to those systems. Cybersecurity has risen out of necessity to protect these vital systems and the information contained within them.
In particular, transportation is becoming more connected and dependent on advanced computing systems and software. Exciting next-generation communications technology – such as connected vehicles that exchange information in real time with nearby vehicles and infrastructure to make travel safer, cleaner, and more efficient – will soon be deployed on roads and highways worldwide. In exploring the potential of connected vehicles and other advanced technologies, we must understand that cyber security has an even more important role - systems, devices, components, and communications must be protected from malicious attacks, unauthorized access, damage, or anything else that might interfere with safety functions.
The distributed ownership, operation, and oversight of the transportation system among national, state, and local governments as well as the private sector imposes complexities for implementing cybersecurity solutions and information sharing in this system.
Today’s vehicles offer an amazing array of advanced technologies that enhance safety, improve efficiency, and reduce environmental impacts. These are accomplished through increased use of electronics and software in vehicle design and manufacture. However, the same capabilities also introduce new risks involving unauthorized access to vehicle systems to retrieve driver data or manipulate vehicle functionality
As vehicle cyber security threats have emerged, the National Highway Traffic Safety Administration (NHTSA) has adopted a research approach focusing on solutions to harden the vehicle’s electronic architecture against potential cyber-attacks and ensure vehicle systems take appropriate, safe steps, even when an attack may be successful. A layered approach to vehicle cyber security reduces the probability of success for an attack and mitigates the potential ramifications of a successful intrusion.
The Federal Highway Administration (FHWA) is working on multiple fronts to improve the cyber security resilience of surface transportation infrastructures. Outreach and awareness efforts are underway in cooperation with the National Highway Institute, engineering organizations, and transportation agencies to demonstrate how cyber security risks can affect their operation. Tools are being created to help interested agencies improve their infrastructure, processes, and organizational structures to more effectively address risk to their cyber physical systems. FHWA’s efforts have focused on customizing risk mitigation materials, originally developed by the National Institute of Standards, for operating engineers in the highway transportation sector. The agency also is working to explore, assess, and mitigate additional risks that potentially could stem from increased connectivity between vehicles and infrastructure.
The U.S. Department Of Transportation (USDOT) has pursued a “security by design” approach to developing the system architecture (Figure 4.5.4) for ITS and connected vehicles — meaning that the entire connected vehicle system (vehicles, roadside components, and communications media) has been designed with the critical goal of cybersecurity in mind.
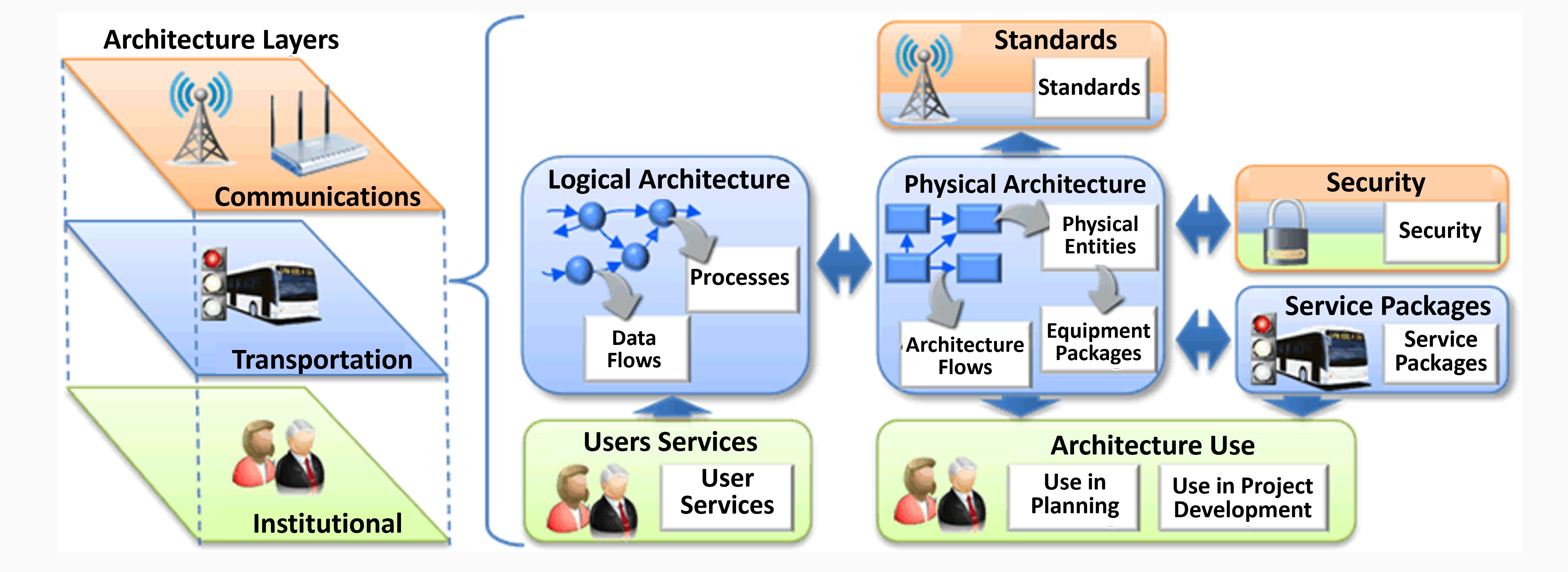
On the left side, there are three stacked levels labeled Architecture Layers, from top to bottom: Communications (orange, icons of a transmission tower and wireless device), Transportation (blue, icon of a bus and traffic signal), and Institutional (green, icons of people). These three levels are bracketed to relate to the elements on the right side of the diagram, which includes seven elements. Starting from the center is a box in blue labeled Physical Architecture, with a flow chart of interconnected boxes directing to "Architecture Flows" and "Physical Entities" which then directs to "Equipment Packages." This center box relates to several items around it. It relates to an element labeled Standards (above, orange, with icon of transmission tower) and another element labeled Architecture Use (below, green, icons of people, with words "Use in Planning," and "Use in Project Development"). The center elements also relate to and from another element labeled Security (orange, blue, green, icon of padlock), an element labeled Service Packages (blue, icons of bus and traffic signal), and an element labeled Logical Architecture (to the left, blue, interconnected spheres pointing to "Processes" and "Data Flows"). An element labeled User Services (green, icons of people) points to the Logical Architecture element above it.)
The vision is to build uniform, end-to-end security into the system architecture to protect the integrity and privacy of the data traveling throughout the connected vehicle ecosystem. This security approach ensures that vehicles exchanging data as they travel down a highway, vehicles receiving data from infrastructure at traffic signals or work zones, and all other components and participants in the connected vehicle system can rely on the integrity of the connected vehicle data received.
The USDOT has supported and participated in the development of voluntary consensus standards critical to the trust/authentication model of security for connected vehicle environments. Organizations such as the Institute of Electrical and Electronics Engineers and the Society of Automotive Engineers develop voluntary consensus standards in cooperation with industry and deployers. The foundational standards required for the USDOT’s connected vehicle security solution have been published and are publicly available. 2