

Disaster response operations require a constant and timely feed of information in order to manage the impacts of cascading events such as traffic incidents and congestion created by planned or spontaneous evacuees or incoming disaster response personnel. Intelligent Transport Systems (ITS) provide tools to better manage disasters and provide situational awareness during the event.
ITS refers to the use of information and communication technologies in transport. The development of ITS is still evolving. The extent to which these technologies are used – and the degree of sophistication in their deployment – varies from one country to another. Transport professionals around the globe need to understand the principal applications and capabilities of ITS so they can assess potential advantages, associated costs and how ITS may best be deployed.
ITS are the control and information systems that use integrated communications and data processing technologies for the purposes of:

Figure 4.5 Kansas City Scout Traffic Management Center monitors regional traffic operations
The definition covers a broad array of techniques and approaches that may be achieved through stand-alone technological applications or through integration of different systems to provide new or enhanced transport services. ITS provides the tools to transform mobility and improve safety – and is particularly relevant in the context of road network operations. 1
The value of implementing ITS strategies into disaster management planning and operations is becoming more apparent as impacts from changing weather patterns, increasing numbers of natural and man-made disasters, and continually increasing traffic volumes create challenges to the functionality and reliability of transportation networks worldwide.
The use of ITS during disaster management operations serves the user of the transport system by providing more reliability and comfort for individual mobility along with more effective operations and decision-making for the operator of the transport system. The overall function of ITS is to improve the operation of the entire transport system - often in real time – for transport network controllers, travelers, shippers, and other users.
ITS deployment is influenced by commercial interests and policy initiatives at the international, national, regional, and local levels – which impact on the business practices of stakeholders in the public or private sector.
ITS provides a flexible approach to addressing common transport problems – one that emphasizes the use of information, optimal decision-making, and a high level of system adaptability. This compares with the more traditional approach of building additional road infrastructure and adding physical capacity. ITS offers alternatives to meeting future travel demand in situations where conventional approaches may not work – for example, in heavily built-up locations or in areas subject to stringent environmental regulations.
More specifically, ITS includes a variety of tools, such as sensing, communications, and computing technologies which can be applied in an integrated way to the transport system to improve its efficiency, safety, sustainability, and the resilience of network operations in the events of serious disruption.
ITS has the potential to relieve some of the most difficult problems that affect road transport today. In general, ITS applications have the capability to:
ITS can also make travel more convenient by providing travelers with accurate and timely information about the traffic conditions on the network and available transport options. Navigation applications such as Google Maps (Figure 4.5.1.1) provide travelers information related to congestion and crashes in real time to improve daily commutes.
It can also foster economic growth in a region by improving mobility, enhancing travel time reliability, and reducing energy consumption.
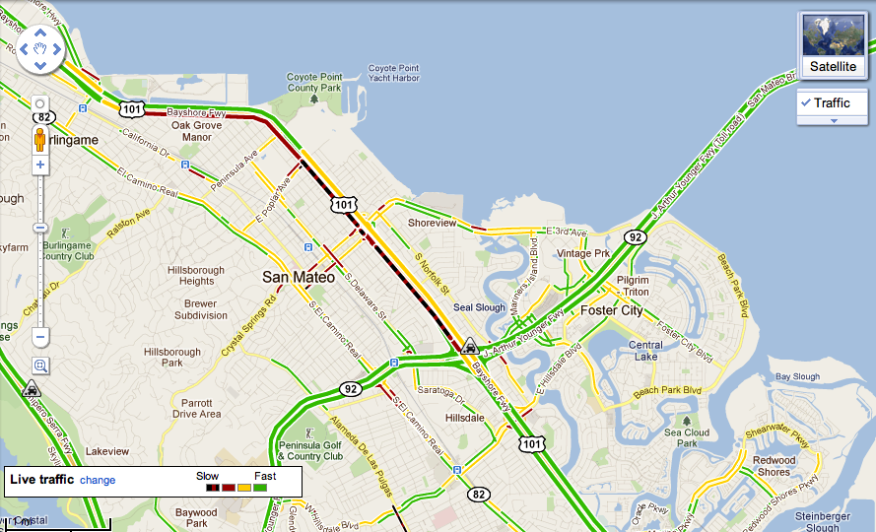
Figure 4.5.1.1 Google Maps live traffic layer
Many ITS applications have a role to play in effective road network operations – the aims of which include:
In general, ITS applications that are designed to improve the efficiency, safety, and/or sustainability of road networks are the applications most frequently adopted. Examples include:
The concept of connected autonomous vehicles is becoming feasible and gaining support – and will have major implications for road network operations – which will need full evaluation. Connected vehicle technology enables vehicles to “talk” to each other by use of in-vehicle or aftermarket devices that continually share safety and mobility information (Figure 4.5.1.2).

Figure 4.5.1.2 Illustration of connected vehicles
All road users – including drivers and passengers, pedestrians and cyclists – across all modes of road transport – including private cars, buses, coaches and commercial vehicles – can benefit from greater use of ITS. For example, ITS applications support:
Most disasters are characterized as short or no-warning emergencies, such as a sudden major storm or other severe weather event, airplane or train crash in occupied areas, earthquake, flash flood or terrorist threat. The less frequent, but usually more devastating events are prewarned disasters, such as a hurricane, tsunami, major river flood, or major spreading fire. The response to these levels of disasters can be very different.
When the transportation system itself is not materially impacted, by a pandemic for example, the transportation system becomes a set of tools for responding agencies. Highways, buses, trains, and even ships and airplanes become a means of avoiding or evading the emergency. As far as traffic operations, and ITS in particular, are concerned, the following are actions that transportation managers can take to assist disaster managers:

Figure 4.5.2.1 Dynamic Message Signs provide information and warning to travelers during daily commutes and in times of disaster.

Figure 4.5.2.2 SSP temporarily closing a freeway lane to assist emergency responders.
When the transportation system is directly impacted, it is less effective in serving the disaster and its managers. This is when preplanning and preparation within the transportation agency are so important. For example, the Florida DOT and several seaside urban areas of the state stockpile traffic signals and generators so they can replace downed signals and control restored ones in the absence of commercial power. PCMS can temporarily replace downed DMS. Portable HAR units can be used for a similar purpose, but these have to be supplemented by fixed signage informing travelers of the HAR station.
There is a need for interagency communications among TMCs, EOCs, and FCs. Unfortunately, this is not always fully achieved because transportation agencies, disaster managers, and security people have different responsibilities and authorities that may seem at odds without structured coordination and open, nonproprietary communication protocols. Open interoperability standards have not been fully achieved in many parts of the world for various reasons.
Equal arguments can be made for including law enforcement dispatch centers in this mix. These groups could communicate by telephone and the internet, but direct electronic linkages for data and information sharing would be better. 1
Disasters may require evacuation of residents and visitors, sometimes from large areas and across multiple jurisdictions. From a traffic perspective, any evacuation is going to severely threaten the capacity of the transportation system to handle it. Most of the actions agencies can take to mitigate the negative impact of an evacuation and help keep traffic flowing require changes in the physical infrastructure or the use of mass-passenger modes. Here are some examples:

Figure 4.5.3 Contraflow evacuation of Houston as Hurricane Rita approaches
One challenge to emergency managers is unnecessary evacuations. Advanced Traveler Information System (ATIS) is another tool for discouraging people from unnecessarily evacuating. ATIS is a system that acquires, analyzes, and presents information to assist surface transportation travelers in moving from a starting location to their desired destination. An ATIS may operate through information supplied entirely within the vehicle (autonomous system) or it can use data supplied by the traffic management centers. Relevant information may include locations of incidents, weather and road conditions, optimal routes, recommended speeds, and lane restrictions, all part of the ITS. 1
The opposite of evacuations is the confinement of people within an area, for example to contain a potential pandemic. In this case, CCTV can show where vehicles are traveling when they should not be, and ATIS can augment public safety notices.
Security threats are not that different from natural emergencies, except that they can cover a broader range of impacts, such as cyber/information technology (IT) attacks; chemical, biological, radiological, nuclear, and explosive (CBRNE) threats and terrorist actions, etc. Emergency and security responders must know the status of routes to and from the threatened area, both for responders and rescue assets. 1
The biggest challenge to the ITS system is a result of the increased value of ITS data and connectivity. Concerns about cybersecurity for ITS and traffic management deployments are related to both current technologies and as legacy systems, coupled with the growing trend to integrate ITS deployments with other networks. This combination has introduced new threats that have not been previously encountered in this domain.
The last few decades have witnessed the pervasive spread of computers, the Internet, and wireless technology. As these systems have become integral to our daily lives, so too has the potential for attacks to those systems. Cybersecurity has risen out of necessity to protect these vital systems and the information contained within them.
In particular, transportation is becoming more connected and dependent on advanced computing systems and software. Exciting next-generation communications technology – such as connected vehicles that exchange information in real time with nearby vehicles and infrastructure to make travel safer, cleaner, and more efficient – will soon be deployed on roads and highways worldwide. In exploring the potential of connected vehicles and other advanced technologies, we must understand that cyber security has an even more important role - systems, devices, components, and communications must be protected from malicious attacks, unauthorized access, damage, or anything else that might interfere with safety functions.
The distributed ownership, operation, and oversight of the transportation system among national, state, and local governments as well as the private sector imposes complexities for implementing cybersecurity solutions and information sharing in this system.
Today’s vehicles offer an amazing array of advanced technologies that enhance safety, improve efficiency, and reduce environmental impacts. These are accomplished through increased use of electronics and software in vehicle design and manufacture. However, the same capabilities also introduce new risks involving unauthorized access to vehicle systems to retrieve driver data or manipulate vehicle functionality
As vehicle cyber security threats have emerged, the National Highway Traffic Safety Administration (NHTSA) has adopted a research approach focusing on solutions to harden the vehicle’s electronic architecture against potential cyber-attacks and ensure vehicle systems take appropriate, safe steps, even when an attack may be successful. A layered approach to vehicle cyber security reduces the probability of success for an attack and mitigates the potential ramifications of a successful intrusion.
The Federal Highway Administration (FHWA) is working on multiple fronts to improve the cyber security resilience of surface transportation infrastructures. Outreach and awareness efforts are underway in cooperation with the National Highway Institute, engineering organizations, and transportation agencies to demonstrate how cyber security risks can affect their operation. Tools are being created to help interested agencies improve their infrastructure, processes, and organizational structures to more effectively address risk to their cyber physical systems. FHWA’s efforts have focused on customizing risk mitigation materials, originally developed by the National Institute of Standards, for operating engineers in the highway transportation sector. The agency also is working to explore, assess, and mitigate additional risks that potentially could stem from increased connectivity between vehicles and infrastructure.
The U.S. Department Of Transportation (USDOT) has pursued a “security by design” approach to developing the system architecture (Figure 4.5.4) for ITS and connected vehicles — meaning that the entire connected vehicle system (vehicles, roadside components, and communications media) has been designed with the critical goal of cybersecurity in mind.
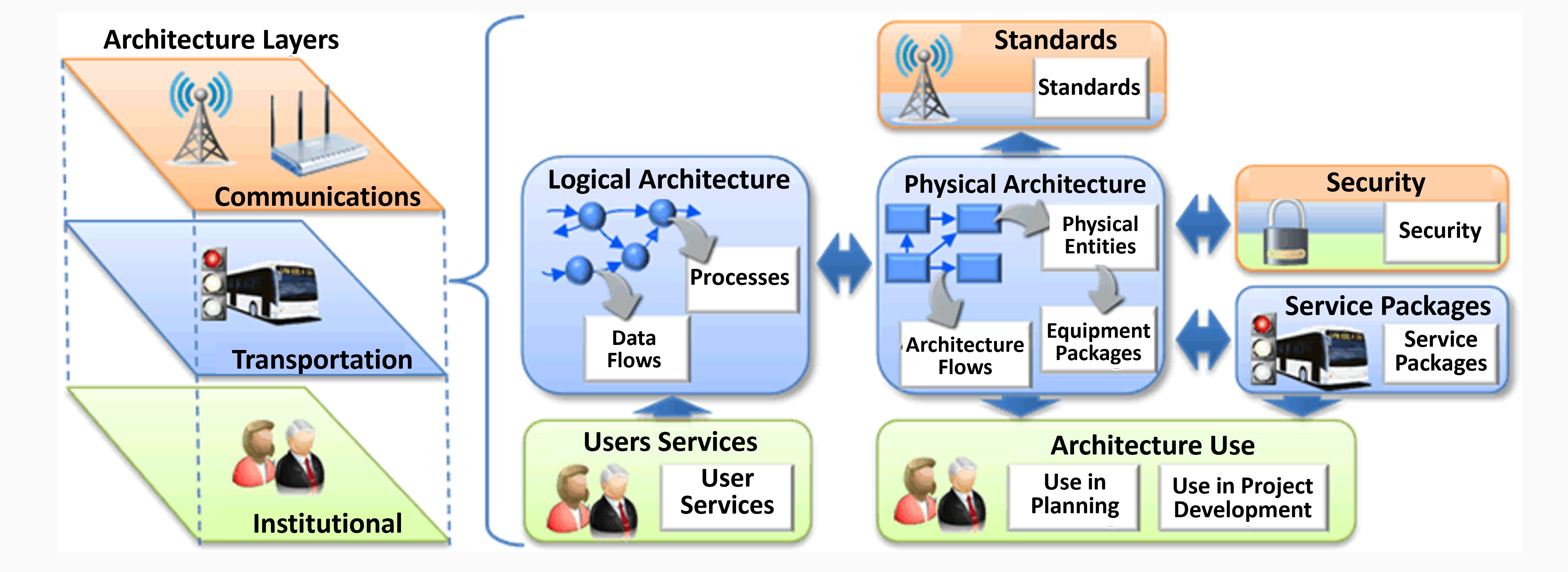
Figure 4.5.4 This graphic illustration demonstrates the architectural view of ITS.
On the side, there are three stacked levels labeled Architecture Layers, from top to bottom: Communications (orange, icons of a transmission tower and wireless device), Transportation (blue, icon of a bus and traffic signal), and Institutional (green, icons of people). These three levels are bracketed to relate to the elements on the side of the diagram, which includes seven elements. Starting from the center is a box in blue labeled Physical Architecture, with a flow chart of interconnected boxes directing to "Architecture Flows" and "Physical Entities" which then directs to "Equipment Packages." This center box relates to several items around it. It relates to an element labeled Standards (above, orange, with icon of transmission tower) and another element labeled Architecture Use (below, green, icons of people, with words "Use in Planning," and "Use in Project Development"). The center elements also relate to and from another element labeled Security (orange, blue, green, icon of padlock), an element labeled Service Packages (blue, icons of bus and traffic signal), and an element labeled Logical Architecture (to the , blue, interconnected spheres pointing to "Processes" and "Data Flows"). An element labeled User Services (green, icons of people) points to the Logical Architecture element above it.)
The vision is to build uniform, end-to-end security into the system architecture to protect the integrity and privacy of the data traveling throughout the connected vehicle ecosystem. This security approach ensures that vehicles exchanging data as they travel down a highway, vehicles receiving data from infrastructure at traffic signals or work zones, and all other components and participants in the connected vehicle system can rely on the integrity of the connected vehicle data received.
The USDOT has supported and participated in the development of voluntary consensus standards critical to the trust/authentication model of security for connected vehicle environments. Organizations such as the Institute of Electrical and Electronics Engineers and the Society of Automotive Engineers develop voluntary consensus standards in cooperation with industry and deployers. The foundational standards required for the USDOT’s connected vehicle security solution have been published and are publicly available. 2
1 PIARC ROAD NETWORK OPERATIONS & INTELLIGENT TRANSPORT SYSTEMS: A GUIDE FOR PRACTITIONERS Professor Mashrur (Ronnie) Chowdhury (Clemson University, S. Carolina, USA), Professor Adel Sadek (State University of New York, Buffalo, NY, USA)
1 PIARC ROAD NETWORK OPERATIONS & INTELLIGENT TRANSPORT SYSTEMS: A GUIDE FOR PRACTITIONERS Professor Mashrur (Ronnie) Chowdhury (Clemson University, S. Carolina, USA), Professor Adel Sadek (State University of New York, Buffalo, NY, USA)
1 ITS Professional Capacity Building Program: ITS ePrimer https://www.pcb.its.dot.gov/eprimer/default.aspx Charles E. Wallace, Ph.D.(Transportation Consultant, Alachua, FL, USA)
1 "Advanced Traveller Information Systems(ATIS) | Intelligent Transportation System (ITS)". Intranse.in. 2010-10-27.
1 ITS Professional Capacity Building Program: ITS ePrimer https://www.pcb.its.dot.gov/eprimer/default.aspx Charles E. Wallace, Ph.D.(Transportation Consultant, Alachua, FL, USA)
2 US Department of Transportation-Intelligent Transportation Systems Joint Program Office https://www.its.dot.gov/factsheets/cybersecurity.htm